Entradas de blog
Ha seleccionado dos tipos diferentes de Download, por lo que necesita presentar formularios diferentes que puede seleccionar a través de las dos pestañas.
Su(s) solicitud(es) de Download:
Al enviar el siguiente formulario, recibirá enlaces a las descargas seleccionadas.

Su(s) solicitud(es) de Download:
Para este tipo de documentos, es necesario verificar su dirección de correo electrónico. Recibirá los enlaces a las Download seleccionadas por correo electrónico después de enviar el siguiente formulario.

Descargas de Utimaco
Visite nuestra sección de descargas y seleccione recursos como folletos, fichas técnicas, libros blancos y mucho más. Puede ver y guardar casi todos ellos directamente (pulsando el botón de descarga).
Para algunos documentos, es necesario verificar su dirección de correo electrónico. El botón contiene un icono de correo electrónico.
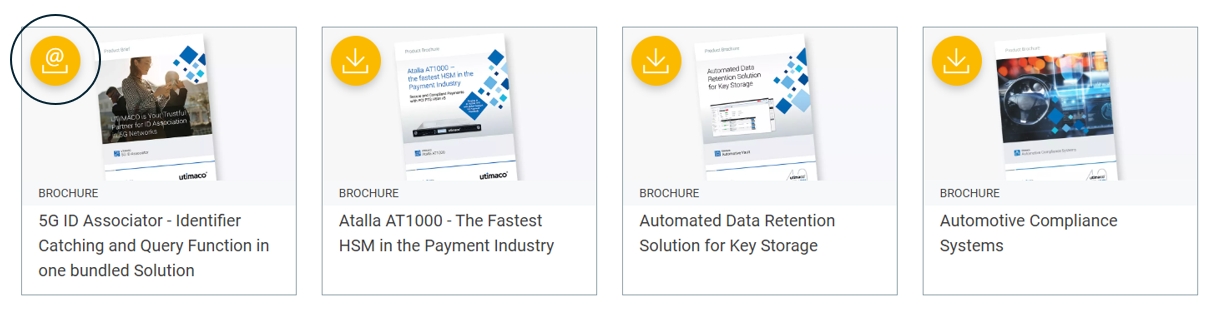
Al hacer clic en dicho botón se abre un formulario en línea que le rogamos rellene y envíe. Puede recopilar varias descargas de este tipo y recibir los enlaces por correo electrónico simplemente enviando un formulario para todas ellas. Su colección actual está vacía.